Cryptography 101
Cryptography 101
I - Introduction
cryp·tog·ra·phy [krip-tog-ruh-fee] noun
- the science or study of the techniques of secret writing, especially code and cipher systems, methods, and the like. Compare cryptanalysis .
- the procedures, processes, methods, etc., of making and using secret writing, as codes or ciphers.
- anything written in a secret code, cipher, or the like.
Definition from: Source
Cryptography. Ciphers. Codes. All of these terms refer to the act (or study) of obscuring messages in some way. It could be to make it harder for third parties to intercept and understand a message, or to more effectively communicate.
Coded messages are often used within the Brotherhood, and are frequently encountered during times of Vendetta.
Given the popularity of the practice, it behooves you to familiarize yourself with some basic ciphers and codes. This course will serve as the foundation of a strong knowledge in the field of cryptography, in turn making you a more valuable asset to the Brotherhood. Down below there will be a brief introduction to the types of Ciphers used with specific interest in each of how to crack it.
II - Monoalphabetic Substitution Ciphers
A substitution cipher is considered the most common type of cipher which it works by replacing each letter of text with another letter. Sometimes these may result in changes with even symbols. A monoalphabetic substitution cipher relies on a fixed replacement structure in which if you have the letter “E” that which has been replaced with “Z”, then it will be true for every instance of the letter “Z” to actually mean “E”. This remains constant throughout the entirety of the message.
The idea is that there is only one alphabet used.
Example of this cipher:

This cipher differs from what is called a Caesar Cipher because the cipher alphabet is not just shifted but jumbled as well. The simple or monoalphabetic substitution cipher is often very easy to crack as the cipher has very little communication security, especially if the message is longer.
Studying the frequency of which a letter occurs in the message, such as the leader E, is called frequency analysis. Using this skill allows for the cipher to be cracked very easily, especially if it were using the most simplest and common letter in written English, E. The longer a message is, the easier it is to study the frequency letters appear.
II.A - Keyword Cipher
A Keyword Cipher is a type of monoalphabetic substitution in which a keyword is chosen and determines the letter matchings within the cipher. Using words or phrases, the creator will encrypt the message based on whatever keyword they choose, leaving you to find out what the keyword is in order to decrypt it. If you are creating it yourself, then you will choose the keyword for the other party.
Example:
if your keyword was "shadow" your cypher key would be:
ABCDEFGHIJKLMNOPQRSTUVWXYZ
SHADOWBCEFGIJKLMNPQRTUVXYZ
The standard example used in this course would look like this:
The Grand Master, the Iron Throne.
rco bpskd jsqrop rco eplk rcplko
II.B Cryptanalysis of Monoalphabetic Substitution Ciphers
With analysing the cipher type from above, you are going to basically calculate the frequency of the letters distributed. Example of how often a letter may be used in a cipher is in the chart below:
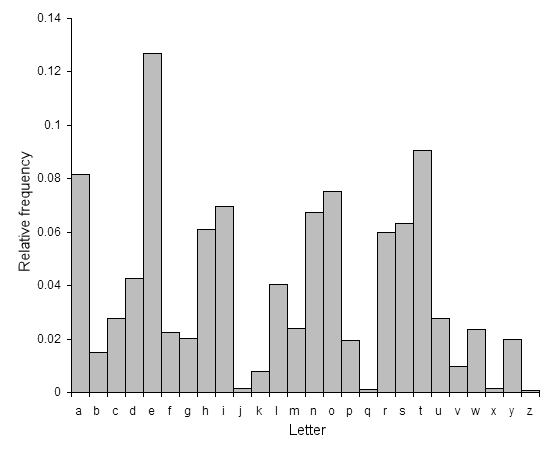
This is the natural distribution of how often a letter appears in the written English language. Based on this chart, the letter ‘E’ is the most common and appears at least 13% of the time. The letter ‘Z’ is around 1% of utilization in the English language. The use of the simple substitution cipher does not change the frequency of these letters in the language. All they do is merely jumble up the letters.
In order to crack the encrypted message, the cryptanalyst basically has to find the ‘key’ used to encrypt the message. Short pieces of text make it more difficult to crack, while like stated before, longer pieces of text make it easier.
| Example | Frequently Used Words |
|---|---|
| One Letter Words | a,I |
| Frequent Two-Letter Words | of, to, in, it, is, be, as, at, so, we, he, by, or, on, do, if, me, my, up, an, go, no, us, am |
| Frequent Three-Letter Words | the, and, for, are, but, not, you, all, any, can, had, her, was, one, our, out, day, get, has, him, his, how, man, new, now, old, see, two, way, who, boy, did, its, let, put, say, she, too, use |
| Frequent Four-Letter Words | that, with, have, this, will, your, from, they, know, want, been, good, much, some, time |
III - Caesar Cipher
A commonly known type of substitution cipher is called the The Caesar Cipher, which is named after Julius Caesar. It said that Caeser used this type of cipher in his communications. The Caeser Cipher is considered one of the most simple and widely known types of technique in encrypting messages. It is like the ROT1 or ROT 4 above, but the rotation is left or right for a number of letters as well as you select how many positions to move through the alphabet to chip the characters in a message. Basically a ROT1 and ROT4, etc. are considered Caeser Ciphers.
Example:
Shifting by 10 characters.
~~~~
The Grand Master, the Iron Throne.
Dro Qbkxn Wkcdob, dro Sbyx Drbyxo.
~~~~
One way of cracking the Caeser Cipher is the brute force attack method, in which you try to decrypt it by trying all possible shifts (25). Another possible attack is to look at the frequency analysis by searching for how often certain characters or sequences of characters appear. When you discover the pattern(s) or the ‘key’, you should be able to crack it.
III.A - ROT Cipher
A ROT, or "Rotate," is a type of cipher where each character in a message has been shifted to the next character in the alphabet by a designated number (generally done to the right of the next letter). This is a very simple cipher, and one that is often taught in schools to amuse children. There may be a rotation of 1 or 5 or even 20 letters in order to create an encrypted enough message. An example of this would be ROT1, which would be a simple shift of each character back one letter.
Example:
ROT1
~~~~
The Grand Master, the Iron Throne.
Uif Hsboe Nbtufs, uif Jspo Uispof.
~~~~
ROT4
~~~~
The Great Jedi War was a farce!
Xli Kviex Nihm Aev aew e jevgi!
~~~~
III.B - Atbash Cipher
The Atbash Cipher is generally used to encode the Hebrew alphabet as a monoalphabetic substitution cipher. It’s a particular type that which reverses the letters in the message, such that "A"s are replaced by "Z"s, "B"s with "Y"s and so forth.
The structure of this cipher in Hebrew looks like this:

Standard Roman alphabet of the 26 letters:

With decryption of this cipher, the one who ends up receiving this message can easily decrypt as it is simple to reverse the alphabet. The cipher only relies upon the alphabet used and the table provided above can be used very easily to decode the message. This type of cipher is better for those message of which have little importance.
To decrypt this cipher, reverse the alphabet again.
Example:
The Grand Master, the Iron Throne.
Gsv Tizmw Nzhgvi, gsv Rilm Gsilmv.
III Frequencies within Monoalphabetic Substitution Ciphers: Decryption and Analysis
III.A Single Letters
Outside of a cipher, which may seem confusing, there is a list of frequently used letters. The letters range within the Roman alphabet from A to Z, with a few being the most widely used.
->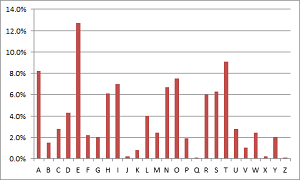
As you can see in the image above, the letter ‘E’ is the most widely used while ‘Z’ is not. This is not a new concept within this lesson, but we will break it down further into different pairings and what we call each pairing.
III.B Digrams
A list of most common Digram, or pairing of letters, is listed here:
of, to, in, it, is, be, as, at, so, we, he, by, or, on, do, if, me, my, up, an, go, no, us, am
III.C Trigrams
A list of the most common Trigrams, a three letter pairing, is listed here:
the, and, for, are, but, not, you, all, any, can, had, her, was, one, our, out, day, get, has, him, his, how, man, new, now, old, see, two, way, who, boy, did, its, let, put, say, she, too, use
III.D Double Letters
A list of the most common double letterings is listed here:
Ll tt ss ee pp oo rr ff cc dd nn
III.E Most Common Words
The of are I and you a can to he her that in was is has it him his
IV Conclusion
There are a lot of common words used within the English language and using them to code the messages you wish to send anonymously requires a bit of skill, but most individuals are able to hide their messages so long as you know which cipher is the easiest to decode. Use the lesson above to take the exam and make sure you read before taking the exam.
Please log in to take this course's exam